Why cybersecurity should be top of mind for machine builders
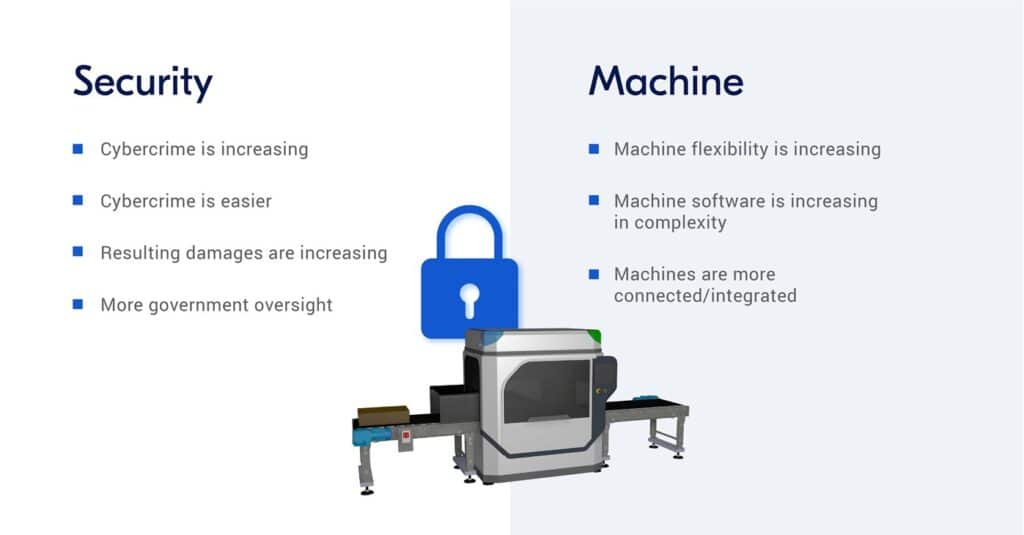
The risk of cyber attacks is growing worldwide as more and more equipment is connected to the internet and machine software becomes increasingly complex. Machine builders must protect their customers and themselves to prevent serious consequences.
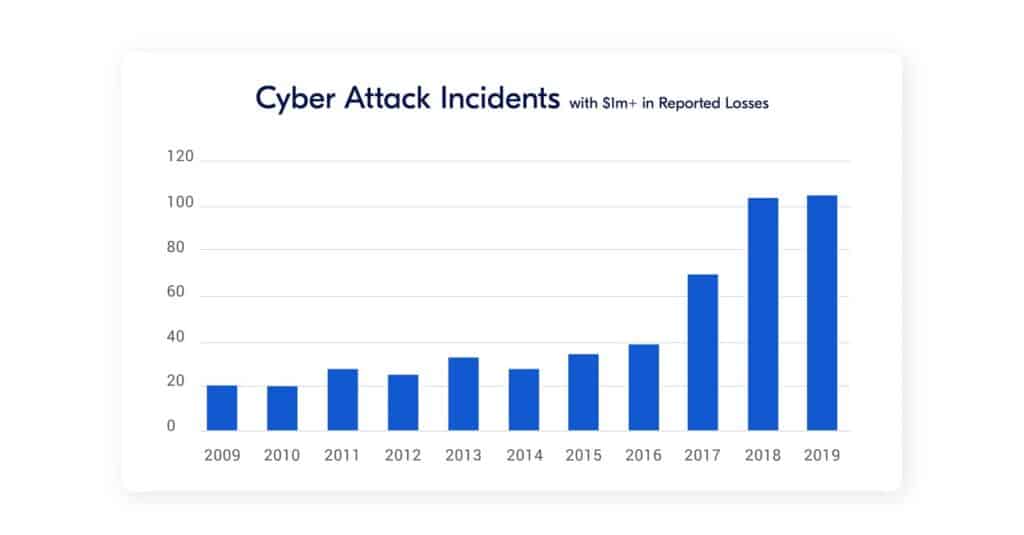
As we venture further into the connected world of Industry 4.0, the likelihood of security breaches and cyber attacks, and the damage they cause, is increasing exponentially. If you are unaware of the security risks, the likelihood of a cyber attack is even greater.
Cyber attacks originating from OT equipment can be disastrous for the factory and cause major damage to your reputation as a machine builder. The number of cyber attacks leading to operational disruption in the industrial sector is increasing dramatically. Machines or even Entire factories are shut down, data is stolen. and in the worst case people get hurt. And all that from, for example, a simple click on a link in a spam email.
Trends in cyber security versus trends in machines
You don't want to be the weak link, so it's time to learn more about cybersecurity and get it sorted. What do you need to know about cybersecurity? How can you take responsibility and what can you expect or ask of your partners?
Increasing customer demand for cybersecurity
End customers, particularly factory owners, are becoming increasingly aware of the risks they face when connecting their equipment to the internet. As a result, they expect more from you in terms of cybersecurity. You need to know how your connectivity solution works and be aware of the risks associated with connected machines. You also need to know how to protect your customer and support them, and you must be able to answer any questions they may have.
However, machine manufacturers offer relatively few service level agreements (SLAs), and there is usually little attention paid to maintenance and monitoring of machines after the warranty period. The main focus is on ensuring that the machines run optimally and are physically safe. This is no longer sufficient, as a lack of expertise on safety measures increases the risks.
That is a lot of extra responsibility in what is, for many machine builders, a completely new field.
Sharing information about your security management
It is clear that machine builders have a significant responsibility towards customers when it comes to the cyber security of their connected systems. You will likely receive questions about the added value of your connectivity solution and how it may impact their factory network. You will gain more trust by communicating and transparent are aware of how security, user access and, for example, open network ports are regulated.
In order to answer questions, it is important to know who is responsible for what in the cybersecurity landscape.
Shared responsibility for cybersecurity
Cybersecurity is a broad topic, and the responsibility for ensuring a securely connected machine is shared by various stakeholders. Unanswered questions about who is responsible for what lead to leaks or attacks. You need to know who should be involved in keeping equipment secure, and what can be expected of whom. Responsibility for cybersecurity is shared by:
- Machine builder
- End customer (user of the machine)
- Provider of connectivity solutions
Responsibilities of the machine manufacturer
The machine manufacturer is the one who decides to connect their machine to a particular connectivity solution. They must ensure that the chosen connectivity solution is secure and cannot cause damage to the connected systems and the OT network. To minimise the risks, you must also:
- Share knowledge gained from monitoring the security of your machine;
- Share information about your security and privacy policy;
- Protect machine components from exposure to external factors with a robust firewall and the latest firmware;
- Manage user access and rights within the connectivity solution.
Responsibilities of the end customer
The end customer must secure their own network and devices, for example:
- Protecting their own IT infrastructure and data;
- Secure devices such as PCs, tablets, and mobile phones with strong passwords;
- Monitoring the identity of the connectivity solution's infrastructure;
- Manage user access and rights within the connectivity solution.
Responsibilities of the connectivity solutions provider
The connectivity solution you choose must be robust and include features that keep connected systems secure, such as:
- An advanced user management system to manage user access and rights;
- Two-factor authentication;
- Strong encryption;
- Backups;
- Robust firewalls.
In the next section, we will take a closer look at what you, as a machine builder, can do in practice.
The most important safety measures that every machine manufacturer must take
To maximise the security of your connected machines, you need to consider various security aspects at different levels. When you start working on cybersecurity, you will want to address the following three topics:
- Internal organisation
- Internal factory network
- Incoming connections
Securing the internal organisation
When we talk about internal organisation, we mean all employees on both the machine manufacturer's side and the end customer's side. Since most cyber hacks are caused by human error, every employee must hacker-proof passwords Employees must be aware of the consequences and the measures they can take, for example through cybersecurity training. In addition, risk analyses, incident management and user management can help to limit the risks.
Securing the internal factory network
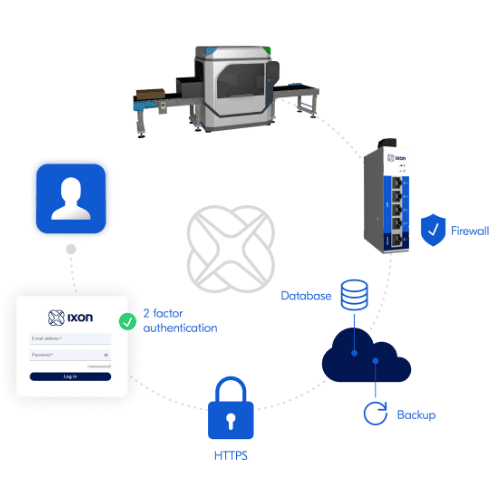
Your machine will be installed in the end customer's internal factory network. First of all, it is important to ensure a secure installation in the factory by means of network separation. Ensure that your machines are protected against unwanted incoming connections by means of a strict firewall, so that they are protected even without regular firmware updates.
Securing the machine against incoming connections
When connecting your machine to the internet, you must ensure that all connections between your machine and the outside world are secure. You should use strong encryption (HTTPS) and it is a good idea to regular penetration tests to carry out or continuously monitor whether your incoming connections are secure. Robust user authentication, such as 2FA, during remote login can reduce the risk of unauthorised access.
Secure both IT and OT
Information technology (IT) focuses on everything related to computer technology, while operational technology (OT) relates to hardware and software used to monitor and control physical devices and processes. OT equipment controls the physical world and IT systems manage data.
OT environments are becoming increasingly dependent on IT. This makes an integrated approach to cybersecurity important, because attackers can now also reach OT via the internet. End customers are already focusing on IT, but there is still much to be gained on the OT side. Both machine builders and end customers need to know how OT security is arranged in a connectivity solution, because that is where many incidents occur.
Consider Shodan, known as a popular search engine for hackers, which is used to discover exposed vulnerable IoT devices, such as routers, SCADA and smart home installations. By exploiting masses of these unprotected devices, attackers can carry out large-scale attacks, such as spamming, phishing and DDoS, which can have a huge impact on you and your customer.
Isolation of both IT and OT is a must. On the OT side, you must isolate machines from each other, so that one machine does not affect another in the event of contamination and to prevent disruptions in the process due to external network activity. The machine manufacturer can influence this by restricting access to the OT side of the factory for the outside world. block with a firewall.
Weighing up the benefits and risks of connectivity
All this may make you wonder: “Is it really worth installing a connectivity solution?” That's a good question to ask yourself every time you connect a machine to the internet. Do the risks outweigh the benefits, and have you taken all the necessary precautions to minimise the risk as much as possible?
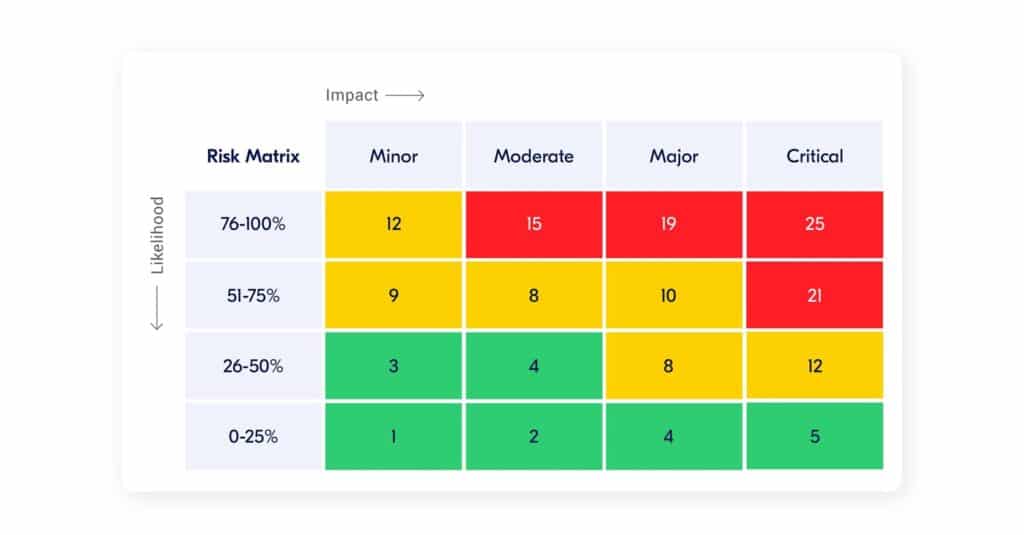
Each additional connected system increases the risk of security breach. To determine whether this is the case, you can assess the risks by weighing up the opportunities against the impact. By explaining why the benefits outweigh the risks, you can convince the customer why connectivity has added value for him.
If the COVID pandemic has taught us anything, it is the immense value of remote access to and control over your equipment. You are the one with knowledge about the machine and the ability to solve problems. By connecting your machines to the internet, you add value by using remote access to your machines and their data to meet your customer's service needs.
You just need to know what the weak points are in your solution so that you can minimise the risks as much as possible. Limit the risks with the greatest probability or impact and keep improving, because new risks arise regularly.
Limiting risks by complying with security standards
Security standards are powerful tools for ensuring that your security, and that of the tools you use, is properly organised. IEC 62443 and ISO 27001 are comprehensive industry standards designed to help companies design secure solutions. The IEC 62443 standard describes requirements for creating safe machine components and how you, as a machine builder, must ensure safe connections. If you work with a cloud service, ISO 27001 is a highly recommended certification to pursue, as it guarantees a strong security focus on data confidentiality.
You may choose to strive to meet these standards yourself, but you should at least work with equipment and companies that already meet them.
Assure your customers of a secure solution
It has become clear that strong cooperation between machine builders and end customers is of great importance in the field of cyber security. Protect both your customers and yourself by investing in knowledge about cyber security, but also focus strongly on having the right (connectivity) partners to help you on your way.
A well-organised IIoT platform can alleviate many security concerns. At IXON, we have built security into our foundation and developed a framework to assist machine builders. Cybersecurity is a top priority throughout the organisation. Everything is taken care of:
- Advanced user management system;
- Two-factor authentication;
- Strong encryption, backups, and robust firewalls;
- Dedicated security officer;
- Comprehensive information security management system;
- ISO 27001 and IEC 62443 certified;
- Internal security training.
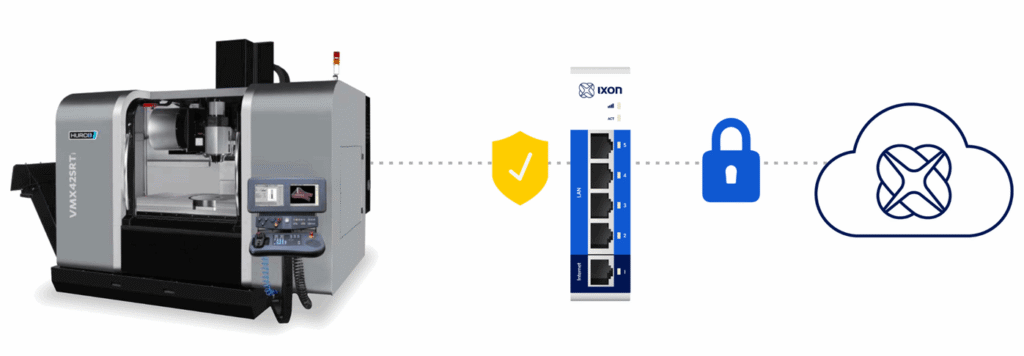
Take advantage of everything a connectivity solution has to offer, such as optimised machines, increased uptime, better service and valuable insights, without having to worry about security. Since it is your responsibility to ensure a secure connectivity solution and prevent damage to connected systems and the OT network, this takes a weight off your shoulders. All you have to do is equip your machine with secure components, manage user access and rights, and share knowledge and information about the security of your machine with customers.
Our security white paper explains the security measures IXON has taken to support machine builders and their customers. Do you need help implementing your security measures? Contact our security officer to discuss how you can ensure your machines are secure.





